STOP DDOS ATTACKS BEFORE THEY STOP YOU.
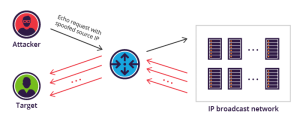
Distributed denial-of-service attacks are on the rise in frequency, sophistication and cost. In 2014 alone, nearly 50 percent of enterprise IT leaders reported experiencing at least one DDoS attack .
So protecting your servers and network – not to mention your customer data, billing records and intellectual property—from a attack is more critical and simpler than ever, thanks to our DDoS protection and mitigation service.
SYS IT DDoS Mitigation Service is a monitoring service that proactively detects and re-routes malicious or affected traffic away from your network to where it can be abandon, so you and your customers experience no downtime or degradation of service.
Certainly if your business relies on the Internet to communicate internally or with customers, conduct eCommerce, or use online bill pay or VoIP telephony, DDoS Mitigation Service is a fortress against illegitimate activity that could save your livelihood.
SYS IT Services are available to protect customers from attacks almost anywhere. Whether your data is hosting inside a SYS IT data center, on-premise at your location, inside a hybrid or cloud environment, or across a third-party network, we have the right solution to stop unwanted traffic from clogging your network. Attack protection is a perfect companion product to:
- Internet Port Customers wanting an additional level of protection across their MPLS network
- Network Customers with assets tied to the availability of their internet infrastructure
- Hosting customers with equipment they want protected in their data centers or ours